By Definition Which Security Concept Uses the Ability to Prove
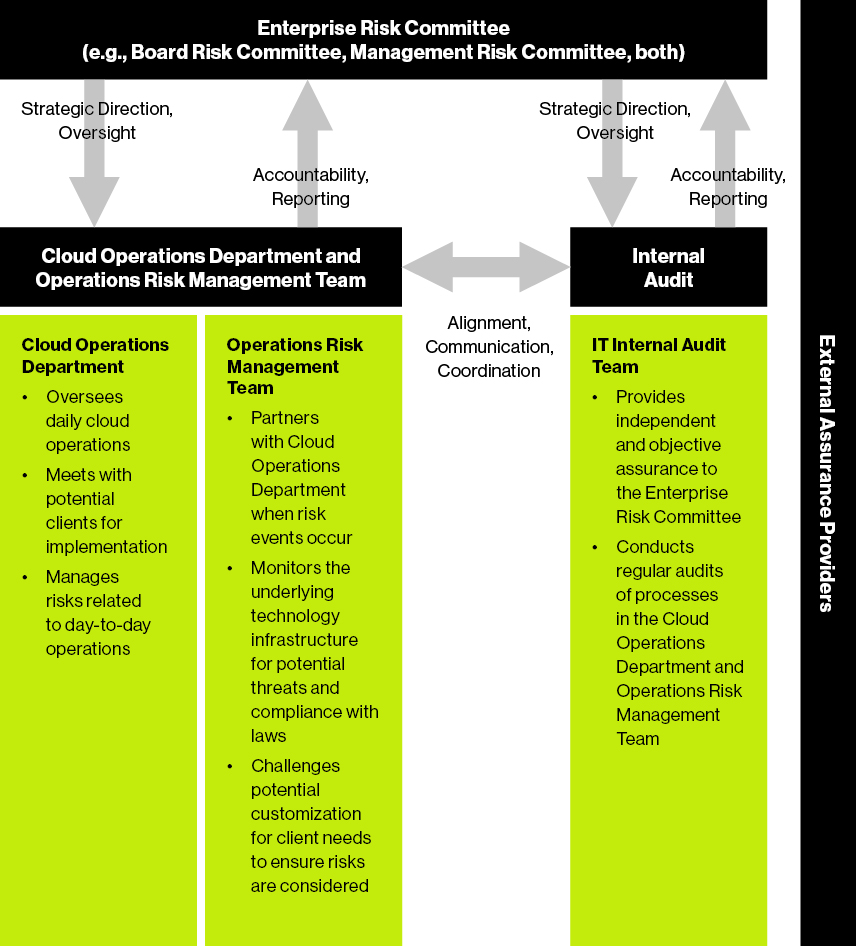
Three Lines Of Defense A New Principles Based Approach Guidehouse
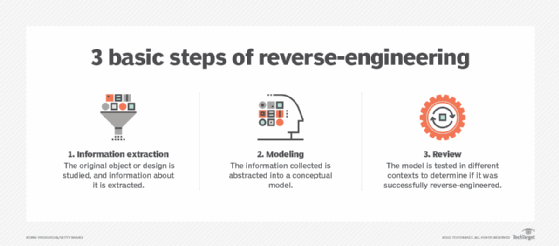
What Is Reverse Engineering How Does It Work
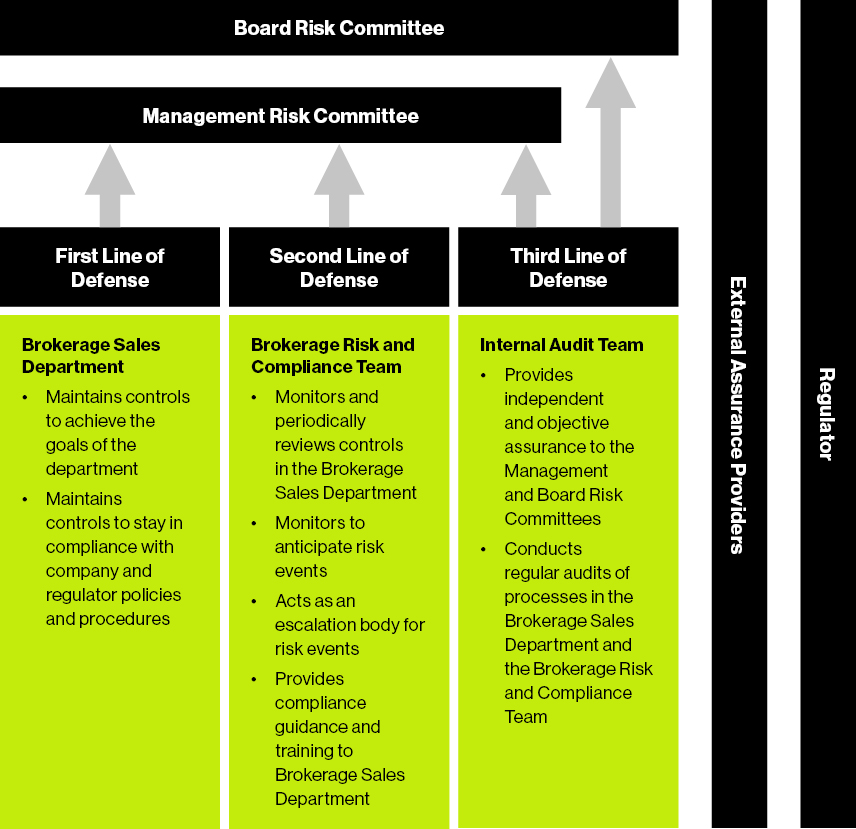
Three Lines Of Defense A New Principles Based Approach Guidehouse
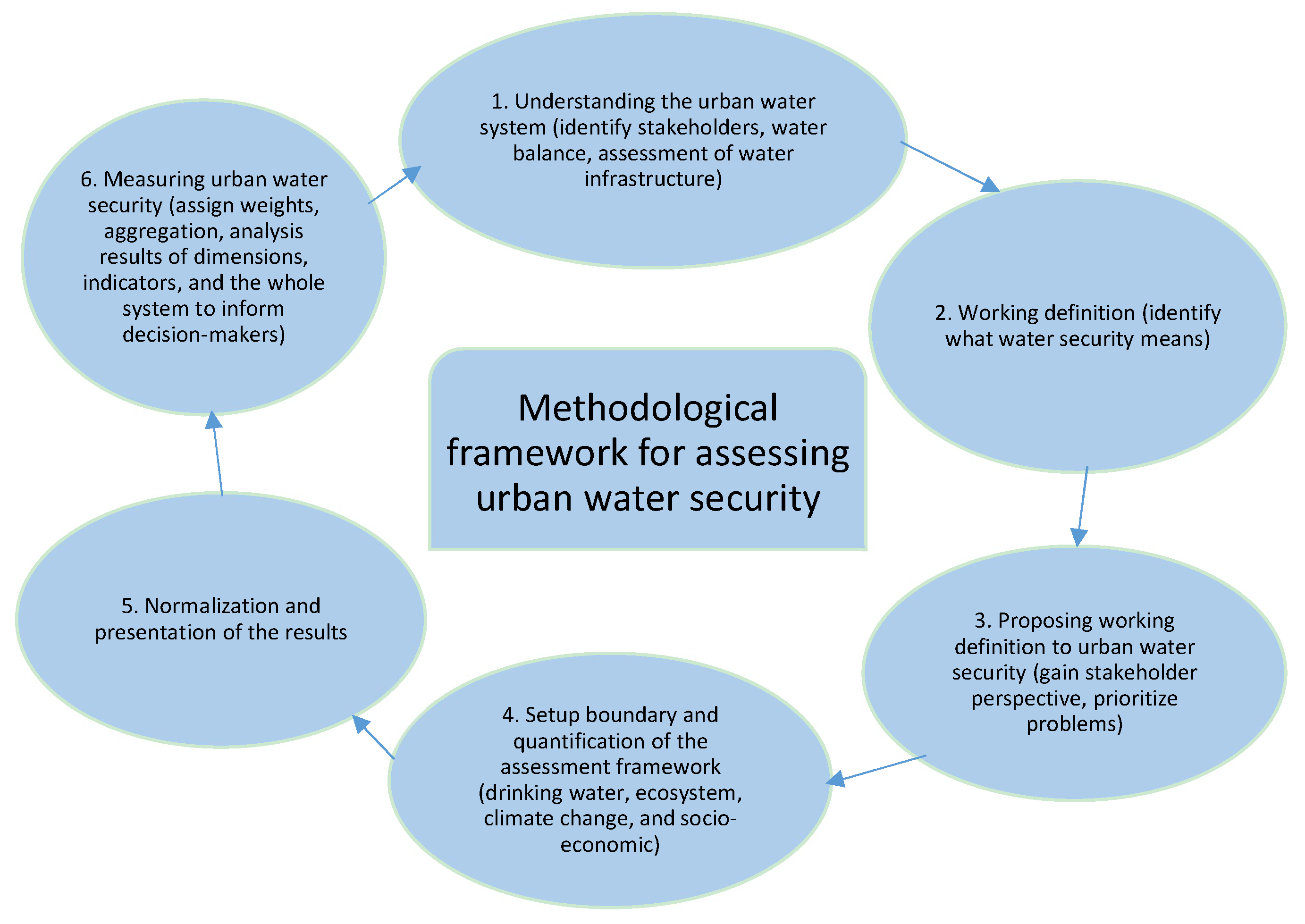
Resources Free Full Text Urban Water Security Definition And Assessment Framework Html
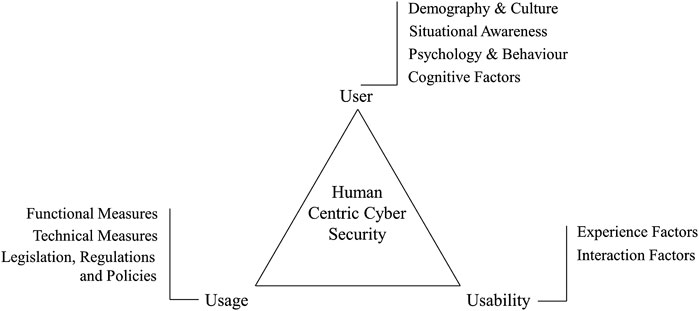
Frontiers User Usage And Usability Redefining Human Centric Cyber Security Big Data
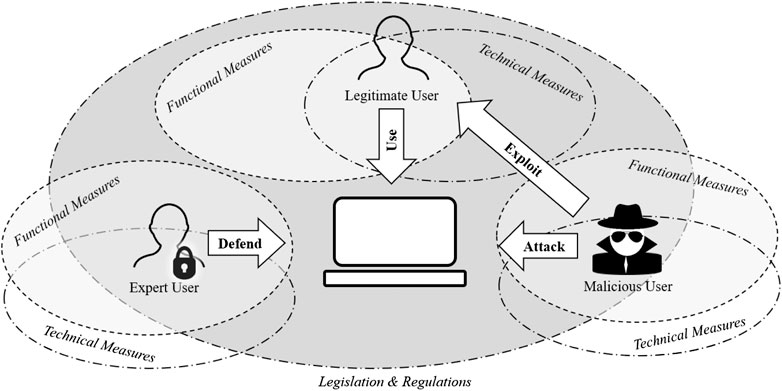
Frontiers User Usage And Usability Redefining Human Centric Cyber Security Big Data

What Is Data Classification Guidelines And Process
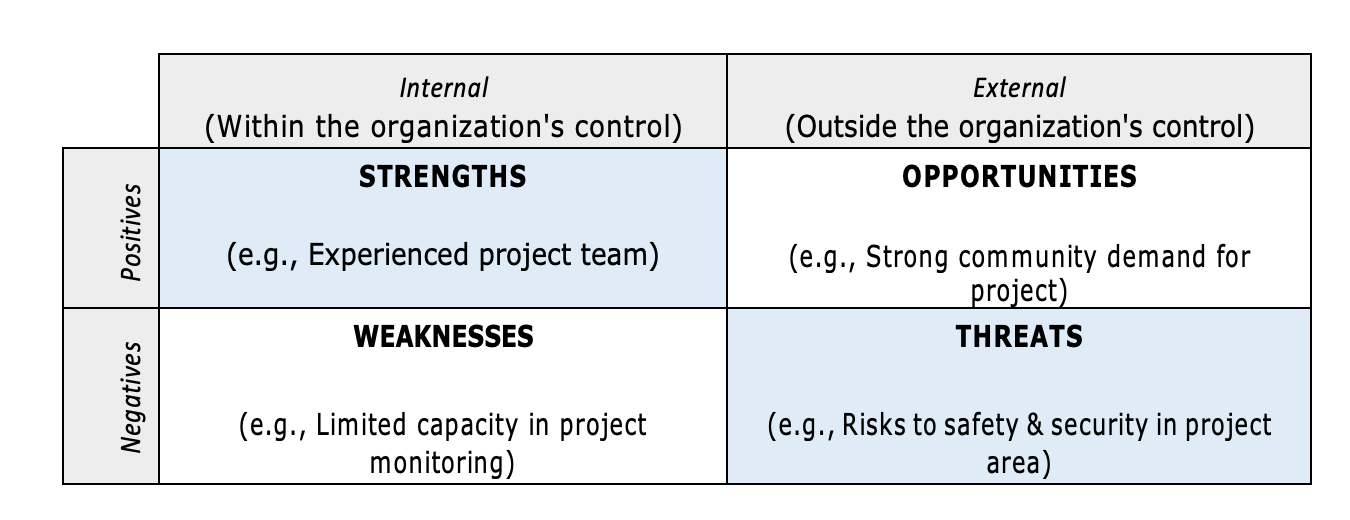
What Is A Project Rationale In A Proposal Funds For Ngos
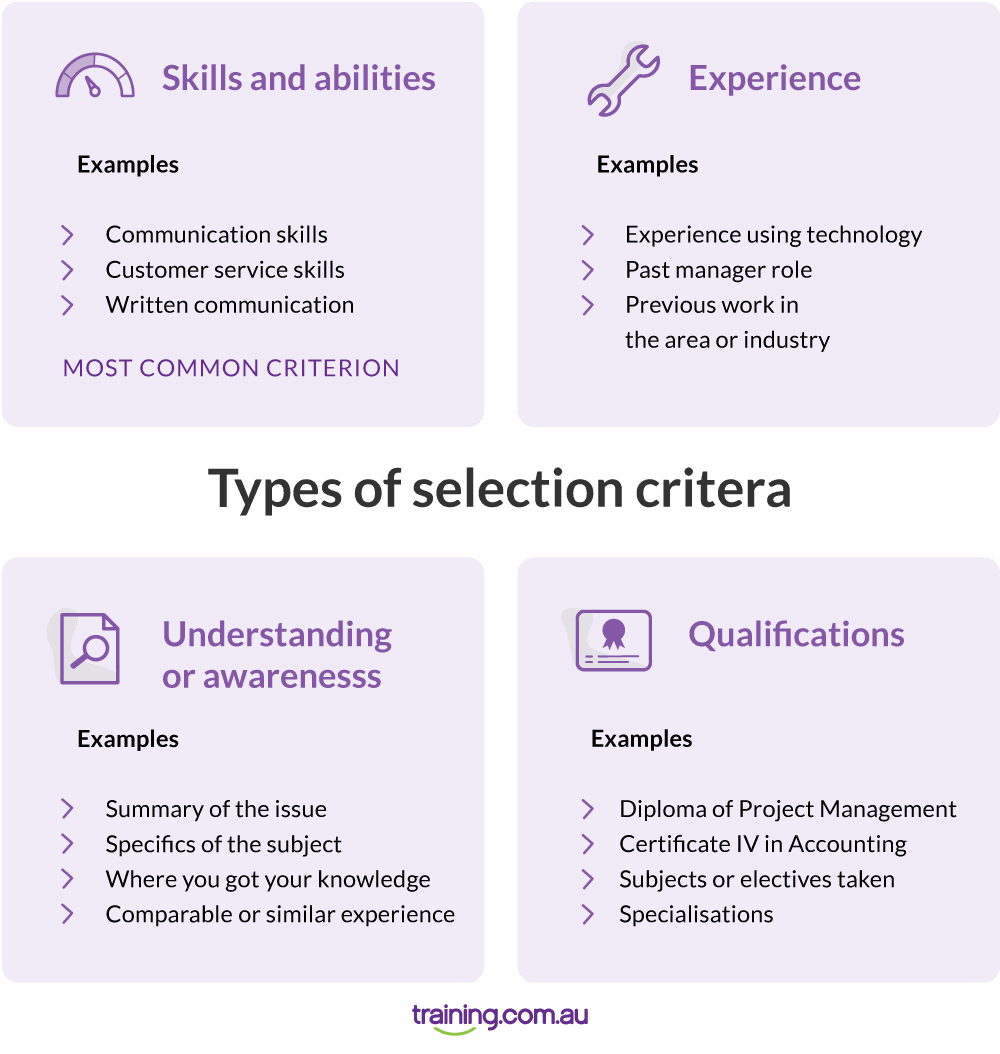
Selection Criteria Examples 13 Good Selection Criteria Responses Training Com Au

What Is A Vulnerability Disclosure And Why Is It Important

Built In Quality Scaled Agile Framework
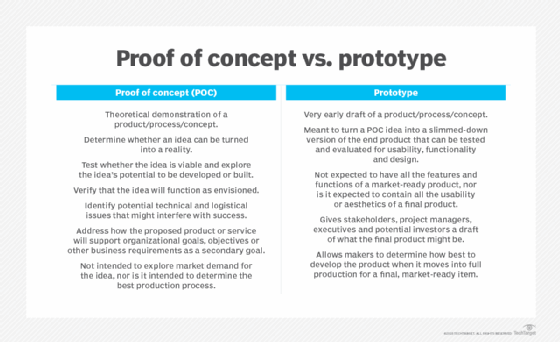
What Is Proof Of Concept Poc Definition From Whatis Com
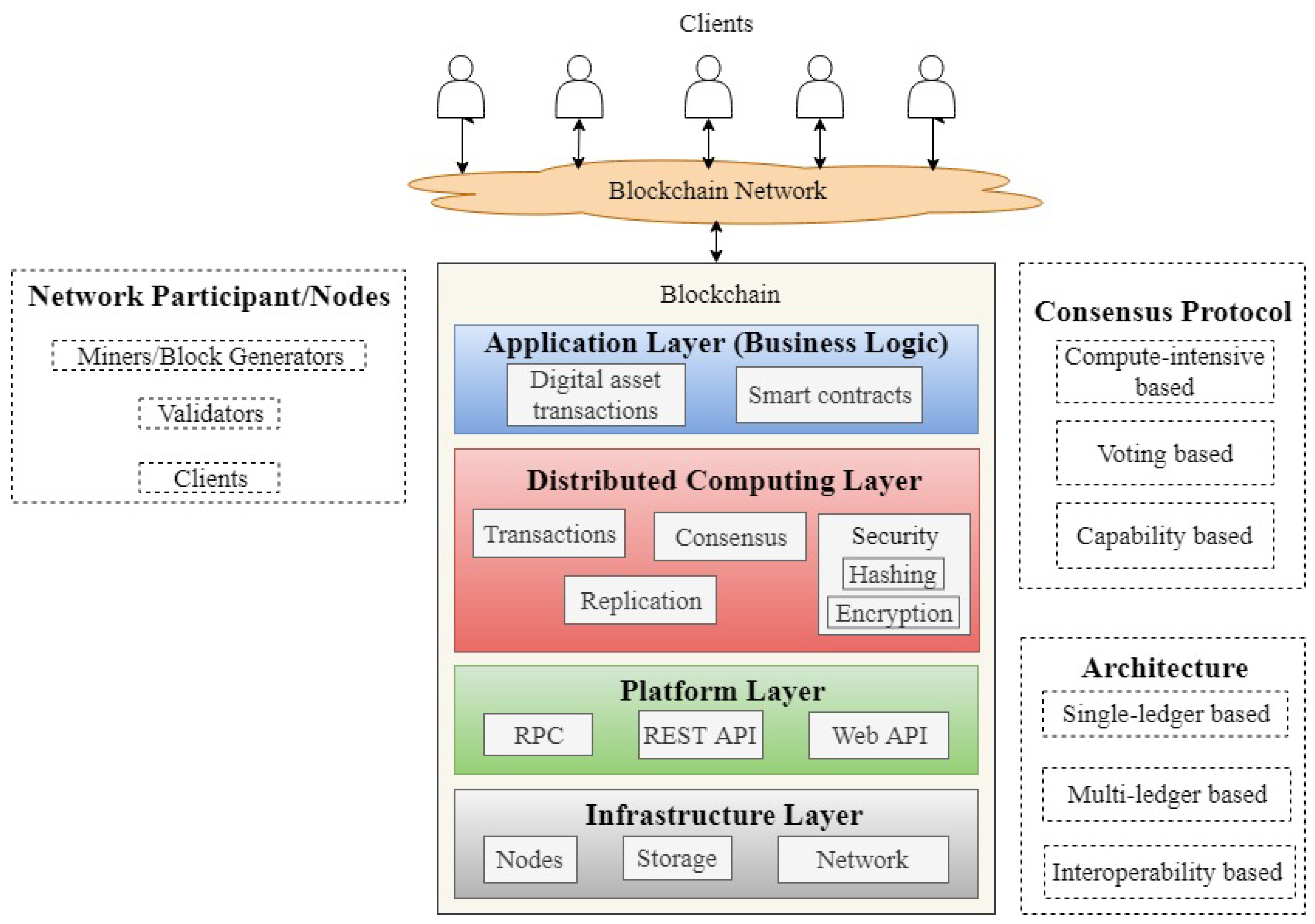
Symmetry Free Full Text A Review Of Blockchain Architecture And Consensus Protocols Use Cases Challenges And Solutions Html

What Is Data Classification Guidelines And Process

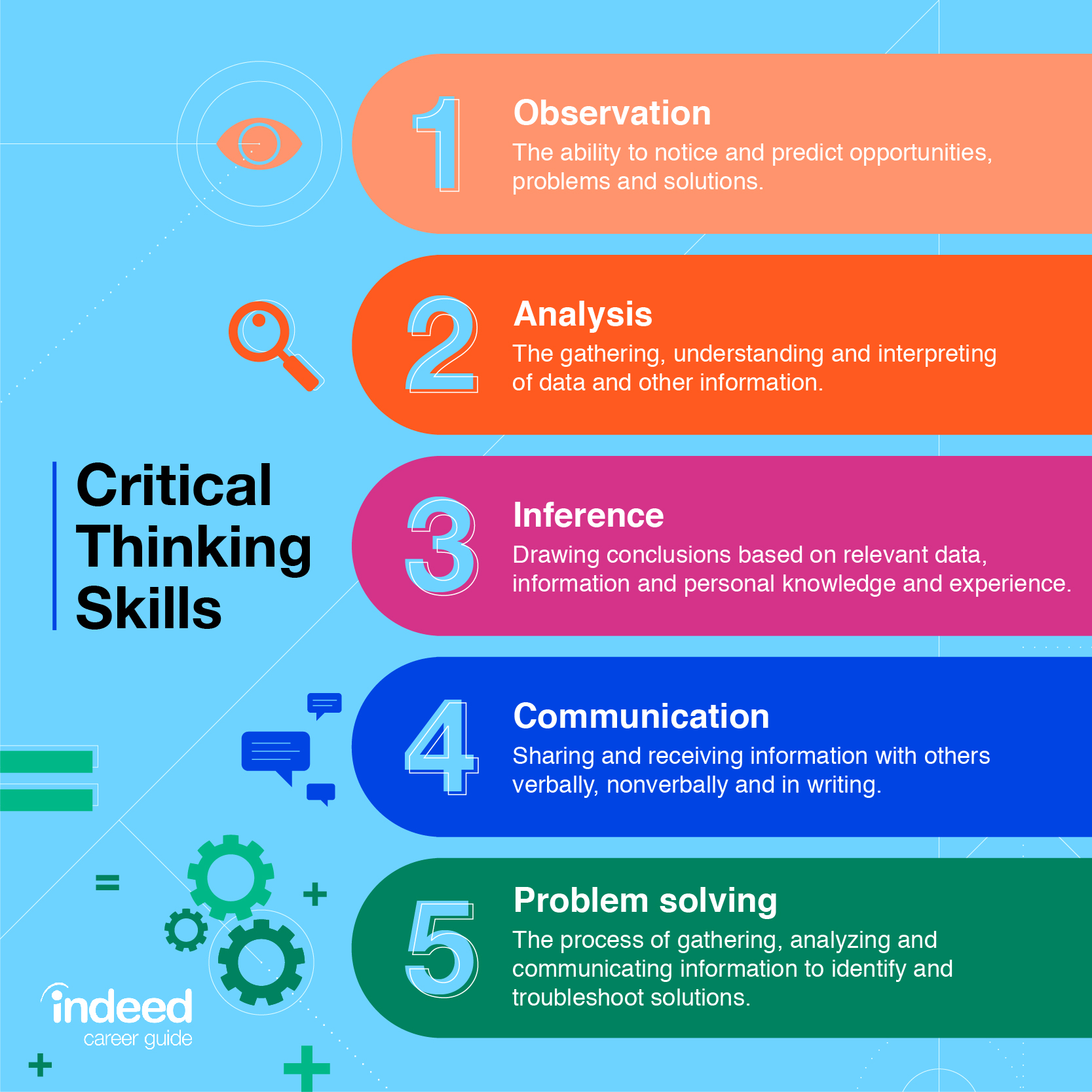
6 Examples Of Critical Thinking Skills Indeed Com
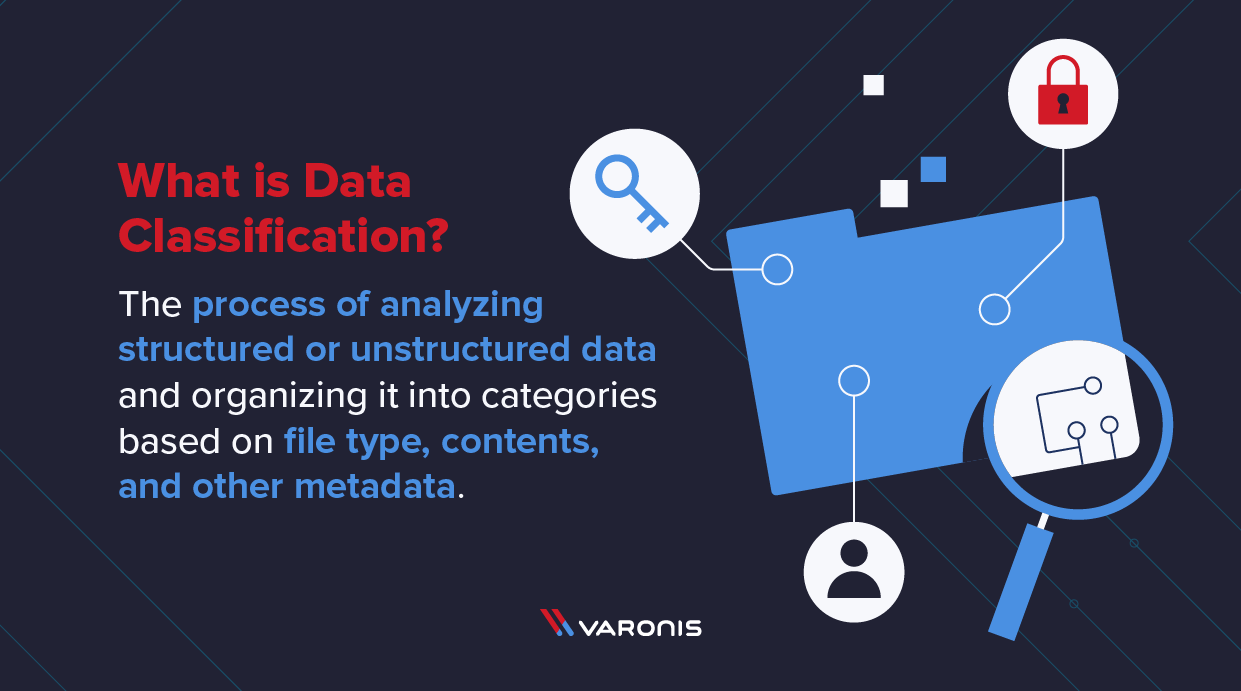
What Is Data Classification Guidelines And Process

Electricity Security Matters More Than Ever Power Systems In Transition Analysis Iea

What Is Siem Security Information And Event Management Splunk
Comments
Post a Comment